News & Insights
We’re Making History in Real Time.
Our timely insights share informed perspectives on the rapidly evolving story of Election Technology, as it unfolds.

Observing International Day of Democracy 2022
The goal of International Day of Democracy is to promote and uphold the principles of democracy. Democracy, at its simplest definition, refers to a government ruled by the people through representatives that have been elected by the whole population. Today is the annual day of observance; our co-founder & COO offers some reflections…

2022 Copenhagen Democracy Summit Recap
This year, the OSET Institute was honored and humbled to receive five invitations to the 5th Copenhagen Democracy Summit, which took place on the 9th and 10th of June in Copenhagen Denmark. It was a remarkable event for which we were honored to attend, participate, co-host a side-meeting, and serve as a co-sponsor...

The Unhandy Logistics of Hand Counts
Fear of technology is like any other phobia: the roots of it are grounded in reality, but the expression of the fear ranges from fantasy thinking to conspiracy theories. The recent push for hand-counted paper ballots (compared to hand-marked) is quickly becoming a repository for the fear of technology. There are several reasons why hand-counting exclusively is problematic…

Piling on the Kraken-Busting of Waldron...
This week the TrustTheVote Project posted an article that is a breakdown/take-down of a slide presentation circulated inside the Trump Administration in the final weeks leading up to 1-6-21. That article combined with some other events this week led us to offer a couple additional points here…

Kraken Busting and the "Most Secure Election Ever"
The November 2020 election has been called “the most secure ever,” for several good reasons, despite the fact that there is still a lot of worrisome room for improvement. Now it appears we may need to crack down on some more Kraken-wannabes before they become such.
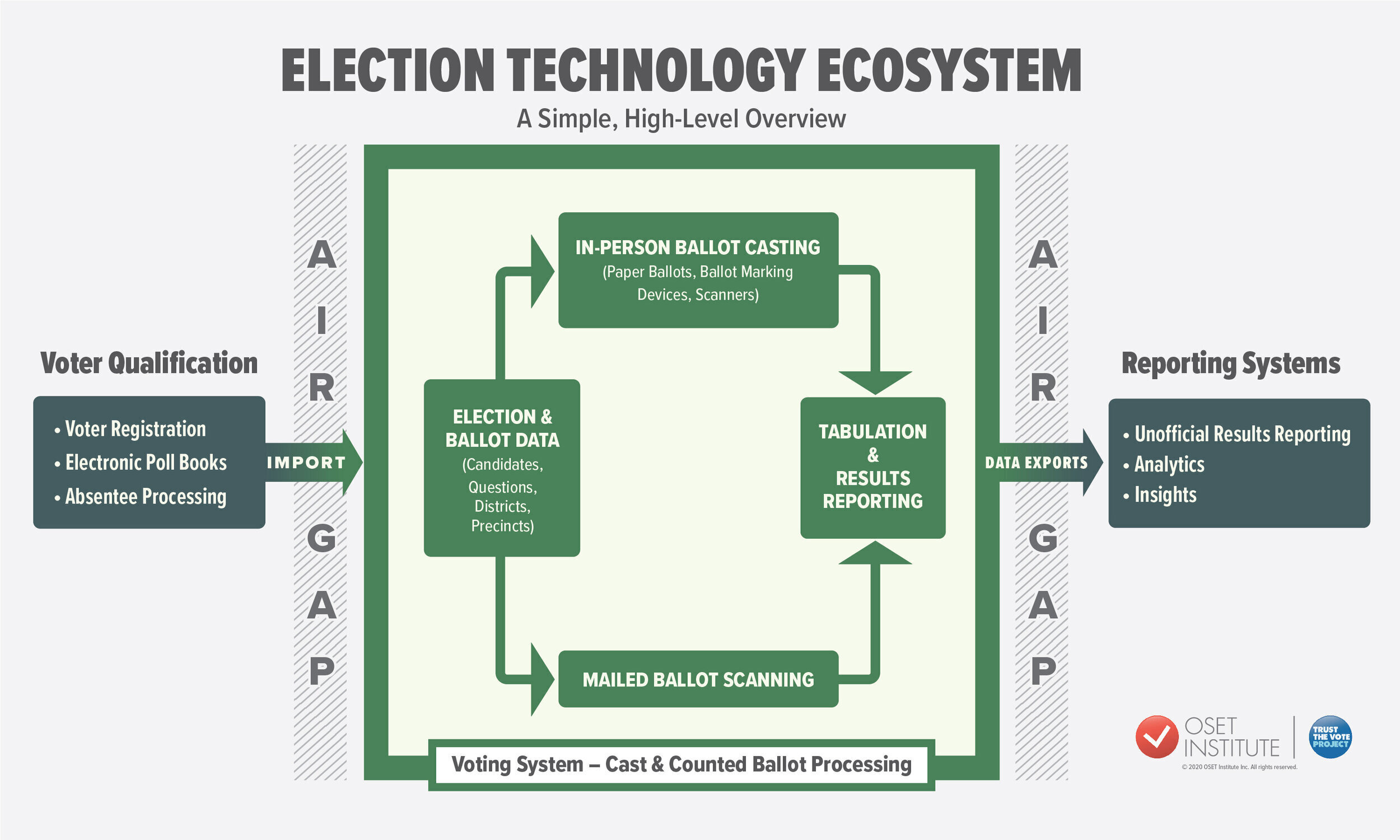
The Basics About the Walled City of Election Administration
Our readers and followers may recall this tweet thread we posted in late November about where votes are counted and stored and how exactly basic voting systems function. The Trump Administration’s persistence of a false narrative about election rigging (“stop the steal”) shows no sign of letting up in the waning days of his presidency. So, it’s time to debunk these claims with an easier to follow explanation (a fact-based narrative) rather than continuing a whac-a-mole approach of pointing out each of the many falsehoods as they pop up, and individually responding. So, OSET Institute co-founders John Sebes & Gregory Miller offer a simple article about what is actually true…

Election 2020: The Most Secure Ever...
Recently, we read Eric Tucker’s and Frank Bajak’s article about the assessment that this election was " the most secure" in American history. (The statement is captured here if the current Administration has removed it). However, we must not believe that “the most secure election” means that there is no further need for government funding or innovation in the existing election technology infrastructure, or that we can just let the status quo remain. We cannot…

Updates on Absentee Ballot Processing in Competitive States
In the week since we launched my Survey on Absentee Ballot Processing, there have been developments and updates as to the absentee process and procedures in the states we highlighted. This article is the main update to the paper as we’re in the closing week before November 3rd, the final day of the election…
Visualizing Election Uncertainty
Our top data visualization wrangler, EJ Fox is now working on a highly relevant and timely effort to gather insights on how to best visualize election data. Longer term, this is part of our data analytics and reporting subsystem work of ElectOS called VoteStream. EJ is focused on how different newsrooms are preparing to visualize uncertainty (e.g., uncounted ballots and more) for the 2020 election. And this work starts with a brief open survey…

Stop the Nonsense About “Counterfeit” By-Mail Ballots – Here are the Facts
The baseless claims that the President of the United States and the U.S. Attorney General have recently made about the possibility of foreign countries interfering with the November election by creating "counterfeit" by-mail ballots are gaining lots of attention, and with good reason. These assertions need to be thoroughly clarified and corrected, because they are not based on facts…

Vote By Mail: A Pragmatic Response to a National Election Hit by COVID-19
As the U.S. battles the spread of COVID-19, expanded Vote-by-Mail is a feasible pragmatic method to help protect the operational continuity of democracy administration and to avoid dangerous disruptions to constitutionally mandated national elections.

House Hearing on Election Security Broaches Supply Chain Issues
The Committee on House Administration, the committee with oversight responsibility for matters relating to federal elections, is holding a hearing today entitled “2020 Election Security: Perspectives from Voting System Vendors and Experts.” The CEOs of the three voting machine makers (Election Systems & Software, Hart InterCivic, Dominion Voting Systems) are providing written testimonies, two of which include statements about supply chain risk. Supply chain risk management is a timely topic.

The Case for Mobile App Voting: Can We Know the Risks to the Whole Election?
In a recent InformationWeek Dark Reading article, Kelly Jackson Higgins asks whether Internet voting by mobile app is better than other forms of Internet voting, based on better security. Rewinding to the beginning of this series: my response is, “No, App based mobile voting isn’t preferable to other forms based on security.” However, it might be preferable to other methods based on voter convenience, but there are many other factors...

National Security and “Federal Control” of Elections
Previously, our CTO, John Sebes tried to unpack the regrettable misunderstanding that current attempts to strength U.S. elections nationwide are some form of Federal hijack of states’ responsibilities for elections. And of course, he is not our corporate lawyer or anyone in Legal trying to sort this out. But from a layperson’s view (at least to Constitutional law and all) this doesn’t seem overly complicated to John, and so here’s his view....

“The Federal government should not gain more control over state elections” — Exactly Right, and Missing the Point
While at DEFCON Voting Village this week, OSET Institute CTO John Sebes observed that there is clearly more energy, more concern, and a greater sense of patriotism about defense of democracy and securing our elections than he has yet to see. And that has John thinking about how the federal government and states’ governments need to cooperate for the benefit of our democratic republic. John comments here, and in a follow-up post.

OSET Institute Returns to Annual Copenhagen Democracy Summit
For the second year in a row, Joy London, a member of the OSET Institute’s leadership team attended the Copenhagen Democracy Summit at the scenic Harborside Royal Danish Playhouse from June 27th-28th. London, the Institute’s Associate General Counsel & Director of International Development, returned to Denmark, where she continued to build the Institute’s network of global democracy advocates, including several members of the Transatlantic Commission on Election Integrity (TCEI) — an organization, launched at last year’s Summit by the Alliance of Democracies (AoD). Here is her fascinating recount of the Conference…
Straight Talk About Election Security Plain Talk
On June 21st the House Administration Committee held a Markup Session for HR 2722 the SAFE Act. We monitor as much of these proceedings as we can. And this one in particular compelled our CTO John Sebes to not only produce a Paper clarifying or correcting several assertions made by a House Member during that proceeding, but also led to a 7-part “plain talk” series on election security posted on our TrustTheVote Project blog. In this post here, John explains why…

The Internet and Elections: Clarifying the Conversation
With the report of comments pouring into the U.S. EAC on the next generation of the Voluntary Voting System Guidelines, and all of the coverage of the issue about the role of the Internet, we feel compelled to try to simplify and straighten some things out. Even recent EAC Hearings have left the issue a bit unsettled and unclear. So, below I try to clarify where things stand as of now in hopes of clarifying the conversation about what is or isn’t.

Microsoft Wades into Election Integrity & Security with New Open Source Software Tools
The primary short-term significance of the Microsoft announcement about ElectionGuard (similar to the recent DARPA SSITH open source trusted hardware project) is validation of a major point about election cyber-security that just wasn’t part of the national conversation a couple years ago: Major technology innovation is required to increase the verifiability, accuracy, and security of elections technology and (at least) U.S. elections. That’s probably just as important as the prospect that ElectionGuard might be included in future proprietary voting system products, or in open-source election technology offerings from OSET Institute’s TrustTheVote Project or others….

New Cybersecurity Threats Require New Thinking on Testing and Certification
Ms. Voting Matters offers a summation of internal leadership discussion on the imperative topic of evolving election technology security; a longer article, but we think worth the read.
On an almost daily basis, there is mounting evidence that the scope of “election security” is wider than might appear at first blush. While much attention has been paid to “voting machines” and “voting systems” that capture and tabulate votes, there is growing awareness that other types of election-related software infrastructure are even more vulnerable by virtue of being network-connected: specifically, voter registration (VR) systems and Election Night Reporting (ENR) systems (which display results over the web, but which do not tabulate votes) have been found to be especially vulnerable. The question is how can cybersecurity testing and certification adapt?
